Saturday, March 31, 2007
Firefox smart keys
1. Back -> Shift + scroll down or backspace
2. Forward -> Shift + scroll up
3. Close tab -> Middle click on that tab you want to close ( or if your mouse have scroll button than click that scroll button on that tab) .
4. Open new tab -> Double click left button on tab bar .
5. Full Screen -> F11 ( don't change screen resolution first try this ) .
6. Decrease Text Size -> Ctrl + scroll up .
7. Increase Text Size -> Ctrl + scroll down .
8. Bookmarks -> Ctrl + b .
9. Find words on specific webpage -> F3
10. Reload page -> F5
This is a list of the most smart shortcuts I use while working on firefox .
Friday, March 30, 2007
Mario and Sonic Olympic Games

In this new Olympic game players will play in events which have different stages and their view would be based on the official venues of the Beijing 2008 Olympic Games . Game contains 100m track, engage in exhilarating rallies in table tennis and churn water in a swimming heat, all while competing for the much sought after gold medal. News via Gamespot .
Thursday, March 29, 2007
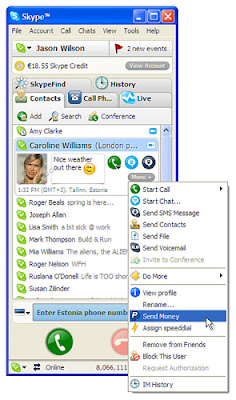
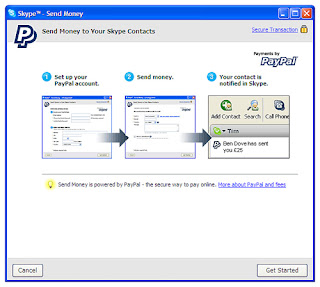
Paypal option in Skype Beta 3.2
It's features is subjected to paypal limitations - Your country must be supported by paypal for sending and receiving money .If you send money to someone where paypal facility is not available than don't worry if that money is not received from receiver than your money will be back to your accounts or credit cards . So it's fine no fear for money lost also .
Super Search Engine

New webfetch allows its users to search multiple leading search engines at once with most relevant results . It provides us search in different leadings like web search , image search ,audio Search,video search , news search , business listings , people finder provider .And if you find a result you want than you can search that website for more pages with same keywords search terms . This is an easy way to find more in-depth information on relevant sites.
Best point is webfetch will allow its users earn ipoints every time you search using webfetch . You can exchange ipoints for a range of products and services.
http://www.webfetch.co.uk/
Take Malware Quiz
This quiz tests your knowledge of five of the most common kinds of malware, the software you don't want on your computer: Trojan, worm, virus, spyware, and adware. Keep in mind that there are at least seven other kinds of malware we know about.
The answers are located at the end of the quiz.
1. Which of the following is most likely to make your computer stop working?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
2. Which of the following is not a stand-alone program?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
3. Which of the following is most likely to send spam emails from your computer?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
4. Which of the following is lest likely to be detected with standard antivirus software?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
5. Which of the following is most likely to come with other malware?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
6. Which of the following is bundled with the peer-to-peer file-sharing software, Kazaa?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
7. Which of the following is most likely to install a "backdoor" internet connection?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
8. Which of the following is most likely to be involved in a denial-of-service attack?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
9. Which of the following is the only malware publicly documented as having been employed by the FBI to bring a suspect to trial?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
10. Which of the following is most likely to steal your identity?
a. Trojan
b. Worm
c. Virus
d. Spyware
e. Adware
Answers:
1. c. virus. Trojans, worms, spyware, and adware all depend on your computer staying up and running. They use your computer's resources to accomplish whatever their designer intended, such as sending emails, displaying advertising, or stealing information from your computer. Viruses, however, are usually created by vandals who just want to damage as many computers as possible.
2. c. virus. Viruses are not stand-alone programs. Just as biological viruses must take over the cells of their host in order to function and reproduce; computer viruses must take over one or more files of the computer on which they are stored. Trojans, worms, spyware, and adware are all stand-alone programs that can run without the help of another application, though they often come bundled with other applications as a decoy, or with other malware.
3. b. worm. Worms are stand-alone programs that are often used to send spam emails, or emails containing viruses. Trojans often contain worms which are then installed for the purpose of sending spam emails, but the worms are what actually send the emails.
4. e. adware. In the strictest sense, adware is rarely patently illegal or destructive, and so antivirus software makers have traditionally avoided treating it as malware. Adware designers are usually large advertising companies with hundreds of millions of dollars, and they take care to insert end-user licensing agreements (EULA) that supposedly mean that the software is installed with permission. Also, adware will not usually do anything more destructive than show advertising. Nonetheless, adware can quickly multiply on a computer, hogging system resources and causing a computer to slow down or even malfunction. That's why most anti-spyware software makers target adware as well.
5. a. Trojan. By definition, Trojans bear other malware within them, just as the mythical wooden worse bore Greek warriors. The malware can be viruses, worms, spyware, or adware.
6. e. adware, though d. spyware, is also correct. Kazaa's developers, Sharman Networks, make most of their money from the advertising shown by the included adware. The adware typically runs even when the Kazaa software is not in use. Sharman Networks has adamantly denied that the adware that comes with Kazaa is spyware, since, like most adware, it comes with an end-user license agreement that says the user grants permission for the software to be installed. In reality, few Kazaa users, until recently, were aware of just how much adware was being installed on their machines (as much as a dozen or more). Plus, the adware does monitor your internet usage, and so is spyware in the strictest sense.
7. b. worm. Worms most commonly install a "backdoor" internet connection in order to send out data (for instance, spam emails or requests to remote servers) undetected.
8. b. worm. Worms, which most commonly install a "backdoor" internet connection on the host computer, are perfect for sending out the millions of server requests needed to achieve a denial-of-service attack. A denial-of-service attack is when a server is maliciously sent so many hits that it is overwhelmed and cannot continue to operate.
9. a. Trojan. The Trojan "Magic Lantern" was famously used to install monitoring software on the computer of a suspect who was later brought to trial partly on the strength of the evidence gathered.
10. e. Spyware. Spyware is malware that collects information from your computer and sends it to another remote machine, so by definition any software that steals your identity is spyware. However, spyware is often installed on your computer by a Trojan, or sent to you by another computer infected with a worm, so other kinds of malware pose an indirect threat of identity theft as well.
This wonderfull quiz was created by Joel Walsh .He writes for spyware-refuge.com about spyware, viruses, Trojans, adware, worms, and other malware .
How To Fix Windows XP Errors
and problems that can occur in Windows XP as there are stars in the heavens it seems...
So we're going to show you how to effectively Repair Windows XP below!
One of the best features of Windows XP is the built in repair feature!
In previous versions of Windows, repairing an operating system error usually meant formatting and reinstalling the whole
operating system, resulting in loss of all of your precious data. The Windows XP repair feature won't delete your data,
already installed programs, personal information or Windows settings. It just repairs the operating system...
Note: The system repair function will remove any updates you have previously installed that are not included on the CD. Any
windows Drivers will also be reverted to their original XP versions, as well as some settings (network & performance
settings may sometimes be reset to their defaults). It may be necessary to reactivate your Windows XP as well. When finished,
you will have to download all of the updates from Microsoft Windows Update, because they are all replaced during repair.
Why would you ever want to reinstall Windows XP?
1. Can't start Windows XP in safe mode.
2. You have problems caused by a recently installed system update (Windows Update, hotfix, Windows XP service pack, or
Microsoft Internet Explorer update).
3. Your problems can't be solved with system restore, or you can't access system restore.
4. You've installed a new motherboard, or made other major hardware changes and need to reinstall Windows.
Of course, if you are just trying to resolve Windows XP errors and problems, and want to save yourself some MAJOR time and
effort...
Repair Windows XP Installation: Step-by-step:
1: Make certain there are no known hardware issues. Windows repair will ONLY fix software problems. Hardware issues can also
cause boot problems (i.e. bad hard drive, memory, CPU, or power supply).
2: Make Sure & Backup Your Data. It's always a good idea to backup your important data before making changes to Windows XP.
Don't worry, if you follow these instructions your data will be secure and there for you when the windows xp repair is completed.
3: Boot from your Windows XP CD. Insert the Windows XP CD into your computer's CD-ROM or DVD-ROM drive, and then restart your
computer. When the "Press any key to boot from CD" message appears on the screen, press a key to start your computer from
the Windows XP CD.
4: A blue screen will appear and begin loading Windows XP Setup from the CD.
Note: RAID/SCSI/Unsupported UDMA users:
You will be prompted to "press F6 to install any third party SCSI or RAID drivers". Most users will not have to press F6, but
if you are running RAID, SCSI or unsupported UDMA controllers, then you will have to have your controller drivers on a floppy
disk. If you are unsure whether you have RAID/SCSI, then simply let the CD load without pressing F6.
When completed loading files, you will be presented with the following "Windows Setup" screen, and your first option. Select
"To set up Windows XP now, press ENTER". DO NOT select Recovery Console.
When presented with the End User License agreement screen. press the F8 key to continue.
Next, Windows Setup will find existing Windows XP installations. You will be asked to repair an existing XP installation, or
install a fresh copy of Windows XP.
If no installations are found, then you will not be given the option to repair. This may happen if the data or partition on
your drive is too corrupted.
Note: If you install a fresh copy, all data on that partition will be lost!
You are almost through! Windows XP will look like it is installing itself for the first time, but it will keep and
remember all of your data and settings. Just follow the prompts, and have your CD-KEY ready if needed.
WARNING: Due to the proliferation of the Welchia, Blaster and other Worm/Viruses that are prevlanet online...be aware that a
Repair Install will leave your system vulnerable. You can get infected within seconds.
Do not go on line until you have enabled XP's firewall first, and make sure and download and run the free and effective
XoftSPySE Spyware remover & blocker on your PC..It is one of the best we've tested!
Don't forget to run Windows Update! (install critical updates first)
Author: Gary Bracken
Want an easier way to fix Windows XP errors? Download the Free RegCure
Registry Cleaner Scan. It found and repaired 822 errors on our test system and boosted system performance by 15%!
Indian tutors will teach UK students online
This firm will recruit Indian university graduates as tutors and provide them six weeks training to understand them companies technology as well as ways to tackle the accent barrier with students . Students are coached via an online platform that is downloaded on to a home computer and includes an interactive white-board , an instant messaging tool and an internet phone system .Under the deal with HarperCollins, the publisher will promote TutorVista services on its titles. Content from Harper Collins will be used by the Bangalore firm for online learning aids.
However, the firm, which sold about 1,000 hours of lessons last month to about 150 students in the UK and firm also operates in the United States, where it has signed up 950 students. It offers sessions covering every subject offered at A-level and GSCE in Britain. However, 80 per cent of lessons that it has sold so far have been in mathematics.
Now India is also getting innovative in education field very fast speed let see what would be the results of these online coaching systems . News via rediff .
Airtel introduced mchek
 Indian telcom company Airtel has announced the introduction of "mchek - Anytime, Anywhere Bill Payment" . An inovative new solution for indian mobile phone users that offers option of bill payment of their post paid number through mobile . Right now this service will be in Delhi and National Capital Region (NCR).
Indian telcom company Airtel has announced the introduction of "mchek - Anytime, Anywhere Bill Payment" . An inovative new solution for indian mobile phone users that offers option of bill payment of their post paid number through mobile . Right now this service will be in Delhi and National Capital Region (NCR).The company says that it is a latest new service is an industry first and allow their customer to sign-up for their services through online and they can pay bill with ease and convenience of their mobile phones .
How it will work :-
1. First airtel customer will need to send mchek to 458 .
2.After sending message they would be asked to enter 4 digit mchek pin ( security number) .
3. After that customer would have to enter their 16 digit credit card number with expiry date and a 4 digit card verification value number . Right now only visa and master cards are applicable . Then they would be successfully registered for the service.
After getting registered and to pay their bills, customers need to type 'PAY AIRTEL' (e.g. Pay Airtel 11111) and then they need to verify through the pin created in the registration process. After the verification of their pin, customers will receive the receipt number (RN) and Authorisation code (AC) instantly and the payment is credited to Airtel billing system simultaneously and to confirm the transaction, customers need to type 'PYMNT' and SMS to 121 to see that the payment has been successful. News from msn.com
Wednesday, March 28, 2007
Radio in mouse
Now this is a high tech internal fm radio which can feature all local radio stations , it has function of automatic scan function which scan stations and save them in . It's sound is also good and price of the mouse is $ 14.99 . Buy it and place it on your desktop , no one guess that it is a simple radio not a pc mouse . Further information of product Mouse Radio .

Photobucket Remix service
You must be a Photobucket account holder and have already uploaded content into your account, only you will be able to remix our content . When you login to our photobucket account you will see remix button in your album .

When you will click on remix button you will find a demo of how to create your own remix Or otherwise you can read tutorail with step by step in easy mode here .
Motorola CDMA multimedia cellphones

The new Razr maxx Ve king has new version in which we expected many marbelous functions like : ultra-thin, EVDO, and 2 megapixel camera with integrated music player and touch-sensitive controls.The new Z6m modal contains slider packs a 2 mp camera , stereo bluetooth 3.5-mm headphone jack to get tethered and it has also 2gb removable memory .The W385 and W355 bring multimedia on a budget with a mix of GPS location services, Bluetooth, and FM radio. To determine the profiles supported by other Motorola devices, visit www.hellomoto.com/bluetooth.
News via - www.engadget.com
Tuesday, March 27, 2007
Nice indian motorola add
Monday, March 26, 2007
Change blog adress
 After having experience of 6 to 7 months in blogging most of the bloggers starts earning good money and they starts thinking and working on their niche topic . Butnow they think for a good blog we need good name address also so they buy own domain names and shift themselves to their hosting .But in blogger after 6 months also we can change our blog address , if you think your blog is quite good than you can get new good niche good name within few minutes .
After having experience of 6 to 7 months in blogging most of the bloggers starts earning good money and they starts thinking and working on their niche topic . Butnow they think for a good blog we need good name address also so they buy own domain names and shift themselves to their hosting .But in blogger after 6 months also we can change our blog address , if you think your blog is quite good than you can get new good niche good name within few minutes .If you want to change your blog address than try this .
1.Login to your blogger account .
2.click on settings .
3.In settings click on publishing .
4.In publishing you will have option names as blog spot address .
5.In that box enter your new desired blog address and click on save button , if that address is available you will get it in few seconds .I have changed one of my blog address .
Sunday, March 25, 2007
6-D movie viewing in india
 India is getting innovative day by day in every trade , so one the best cinema company Adlabs Cinemas is trying to bring the 6 dimensional viewing experience to India and this method sure revolutionize the way of watching cinema .In the 6-D movie, viewers don’t just experience height, width and depth of a shot (as in 3-D films), but will also be able to smell, touch and feel what’s happening on the screen.
India is getting innovative day by day in every trade , so one the best cinema company Adlabs Cinemas is trying to bring the 6 dimensional viewing experience to India and this method sure revolutionize the way of watching cinema .In the 6-D movie, viewers don’t just experience height, width and depth of a shot (as in 3-D films), but will also be able to smell, touch and feel what’s happening on the screen.Main catch is that the begining of 6D is not going in Delhi or Mumbai but will be in Agra .Because COO of Adlabs says Agra is a hot spot for tourists international and domestic both .
So Indians get ready to fell the real experience of cinema by the end of this year .
News from- Msn.com .
Saturday, March 24, 2007
New ZoneAlarm 7.0.337 released
Functions :-
1. Internet lock - Internet lock blocks Internet traffic while your computer is still or while you're not using the Internet working on any document
 on computer , and it can be activated automatically with your computer's screensaver or after a set period of inactivity.
on computer , and it can be activated automatically with your computer's screensaver or after a set period of inactivity.2. A firewall - A firewall helps protect your computer from hackers on the Internet.It controls the door to your computer and allows only traffic you understand .
3. An application control - The application control allows you to decide which applications can and cannot use the Internet.
4. Zones - Zones monitor all activity and alerts you when any program try to connect your computer to internet .Zone Alarm 7.0.337 is the best pc security software online and it is free for individual and not to profit users on cnet.com . Download link - ZoneAlarm 7.0.337 .
Friday, March 23, 2007
Thursday, March 22, 2007
Google offering homepage themes
Name of themes google providing now are
- Classic
- Beach
- Bus Stop
- City Scape
- Sweet Dreams
- Tea House
- Seasonal Scape
These themes change automatically with climate and day duration like example in morning you will see sun rising scenes pictures and in evening sun sets down and characters in the bus stop theme will hold umbrellas if it is raining.
Wednesday, March 21, 2007
The Blogger Project
How it will work :-
Once in a week Darren will reply to his visitor and other project readers that what tricks he have used and by those method how much traffic he have received , he will tell you his traffic statistics and as well as the income generated by those implemented tricks also . Darren want that other bloggers take part in this project and share their techniques with other bloggers and help them , if it works than with in a week we will share our success and failures .
How to join : -
We don't have to fill any big forum for joining this project , right one comment to Mr Darren that you are interested in this project and that's all . The Blogged Out Project
Even one good thing is that this project will run for 3 months and the total money generated during this period on his blog , he will donate 40% of gross income to a charity which will be voted by all project member at the end of this project . So friend's i have joined this project and you should also , let's gain some more knowledge from it .
Tuesday, March 20, 2007
Insert image in yahoo mail signature
1. Sign in your yahoo mail account .
2. Than click on options button located in right hand side .
3. Than click on signature option .
4. Now click on colour and graphics , it must be on Plain .
5. Now you will see html-navbar above signature box .
6. Select option View HTML Source ,situated below signature box
7. 7. Now insert image using html tags .
8. Replace the image url with yours but remember image shouldn't be higher than 75 pixels .
9. When you finished with your url work , now uncheck View HTML Source
10.When you uncheck that view HTML source option you will be able to see result in signature box . And don't forget to click on add signature to all outgoing mails .
Now click on save button . First send one email to your another email id's and check the results .
Monday, March 19, 2007
TVU Player 2.3
TVU feature some special channels like international sports, lifestyle, news, and your favorite channels from around the globe as well as user-generated content.
Featured channels :- ABC , CBN (Financial) , CCTV , CNN , Cartoon Network , ESPN , HBO and more.. .
Saturday, March 17, 2007
Satyam launches virtual learning world
 Satyam Computer Services Limited on Thursday announced that it has implemented an organisation-wide, virtual learning environment called Satyam Learning World.
Satyam Computer Services Limited on Thursday announced that it has implemented an organisation-wide, virtual learning environment called Satyam Learning World. The holistic approach to learning considers the entire lifecycle of human capital management, and includes critical elements such as induction, entry-level training, continuous competency development, performance evaluation, and career-path development.
SLW is also designed to prepare Satyam professionals to excel at the project and service offering levels, and to work more effectively with partners and customers.
The launching of SLW coincides with Training Magazine ranking Satyam No 15 in its annual listing of the Top 125 organisations for training.
Satyam will invest more than $8 million in the comprehensive program over the next five years Investments and assets will include-tools and technologies such as a learning management system, a content management system, a virtual classroom tool, a performance evaluation management tool, and a networking and blogg OCR tool.
Other tools will handle attendance, library management, web radio, web television Insert Comma and mobile learning.
A database for attendance and evaluations management is also planned . News from Business Standard .
Friday, March 16, 2007
World's Smallest UMPC
 Digital Cube says that their i-Station G43 is the smallest UMPC available, and the - apparently - french guy doing the interview not only believes them, but he seems to be wetting his pants with the excitement of it all in this video. I don't know if I would be excited about the prospect of running Windows XP on a AMD Geode LX800 processor with 256MB of RAM, but hey, whatever rocks your world.
Digital Cube says that their i-Station G43 is the smallest UMPC available, and the - apparently - french guy doing the interview not only believes them, but he seems to be wetting his pants with the excitement of it all in this video. I don't know if I would be excited about the prospect of running Windows XP on a AMD Geode LX800 processor with 256MB of RAM, but hey, whatever rocks your world.In any case, this UMPC runs a full Windows on its 4.3 inch 800-pixel wide screen, and comes with up to 60 GBytes hard drive, Wi-Fi, Bluetooth and a USB Host port. All for only $700, including the XP license, which Digital Cube says you can then trash and install Linux.
News from gizmodo.com and image is taken from engadget.com .
Thursday, March 15, 2007
Increase net Speed 5 times
But the best part of it we can us it in GPRS , DATA CARDS , Now surf on your notebook also like broadband speed . With GPRS , TATA cards and other wireless connections it works like wonder speed giving you over 6 times the speed you were using earlier . It also reduces your download billings inf you are on your per MB download billing basis.More information on jetbrowse .
Wednesday, March 14, 2007
New software for deployment of poll officials
This software has been created to take all burden of deputing people on poll duties from the district magistrate .Group of NIC has started working on this software by following the directions of election commission .
Till yet , work of deploying officials for poll duties was done by DMS which use individual logistics and other resources and because of that there was no uniformity in the allocation of work and distribution of resources. The new software will help in streamlining the work.
EPDS is a data entry software, whereby the work of allocating duty as per the rules issued by the EC will be done by the software once the list of officials is fed into the system.
The new software will ensure that officials either working or residing in a particular Assembly constituency would not be deployed in the same constituency to ensure fairness.News via - rediff .
Method to stop spam email
 Whenever we open our mailbox and finds over 50 to 60 spam mails from out of 70 .This problem is increasing day by day , because their so many programs and people which collect your email id's from groups or forums and than sell to webmasters and online marketers and they start filling your email boxes .
Whenever we open our mailbox and finds over 50 to 60 spam mails from out of 70 .This problem is increasing day by day , because their so many programs and people which collect your email id's from groups or forums and than sell to webmasters and online marketers and they start filling your email boxes .But there are few free methods for fighting again spam. Try these methods to gt ride of this problem .
1. No Response - Don't ever respond to such messages because when you open such messages and click on given links , this makes webmaster sure that your id is active and you are using it .
2. Use mail washer - Get it from mailwasher.net which allows us to view email we receive before downloading it . It helps us to delete many emails including viruses before getting downloaded .
3. Filter option - Use filter option which easily filter emails containing spam and adult words like
sex, viagra .... etc .
4. Personal id - Never post your personal email id or business id in forums and other public places , create one special email id for public use .
Specially never fill forums telling you win or earn money , such kind of forums are 80% fake , just created to grab mail id's , my personal experience my one yahoo email id is having 49,000 emails right now .
Make windows startup fast
1. Click on RUN and type "msconfig" and click ok .
2. Now new window will open , just go to "Start up" option .
 3. Now here you will find the list of programs which usually starts with your window , so remove the tick mark from those programs which you don't want to get started with windows . like nero , adobe check , yahoo and msn messenger and all those you don't want to get started .
3. Now here you will find the list of programs which usually starts with your window , so remove the tick mark from those programs which you don't want to get started with windows . like nero , adobe check , yahoo and msn messenger and all those you don't want to get started .Remember do not remove tick marks from antivirus and others folder about which you don't know , it may harm your computer .
4. Now click on ok button and after that you will get a option for restart your computer apply on it .
5. Click tick mark on the box for don't show this message again , this message you will find when you restart your pc .
Sunday, March 11, 2007
Windows Auto Playlist
1. Click on " my computer"
2. Click on "c:\"
3. Click on "document and settings"folder.
4. After that click on your pc admin user name ( there would be two options all users and one would be your name like John like my is atul , just clik on that name .) folder.
5. Than in last click on "Start menu" folder.
6.Click on "Programs" folder.
7. Click on "Startup"folder .
Here you will find a blank page , just copy your song playlist here and than refresh and now you can restart your pc after booting when you come to windows screen your window media player automatically start playing that song list which you have pasted in startup folder .
I have pasted my own list and my 1st song is a prayer than after that rocking music , it fells good to hear prayer 1st , because pc is also like god which is providing living to so many bloggers
Saturday, March 10, 2007
Are You Pirated
Piracy is the biggest problem for software companies specially for worlds famous company like Microsoft which is owned by worlds richest man Mr Gates so what about others .There are few examples why people like piracy because pirated products are very approx 80 % cheap compared to genuine and many pirated sellers provides you all facilities with cracks and make there product same like genuine .My all friends pc are mostly operated by pirated windows of RS 100 TO 150 and works fine than why i have to purchased Windows xp home edition for Rs. 4,250.00 from ebay or any other shop.
Just go and search ebay website you can get everything but are those things genuine . Yesterday i searched for GTA and i got very impressive results which can make anyone take out his credit card and pay on the spot . Result were like this
GTA San Andreas and GTA Vice City Both pc games cd only for RS 70 (almost $ 1.6) and shipping cost 80 ($ 1.78) . Total Rs 150 or $ 3.36 , Hurry up Quantity only 9 available .
And one website says GTA 3 is for $ 12 Indianplaza .So there is a large difference and why public will gonna buy genuine one .
This is paid piracy but there are few buddies which makes loss to both pirated sellers and companies , they simply tell you to download free trail period and than provide you keys or cracks of that software for few little amount like $ 1 or $ 2 .
Softwares companies says that they are getting huge profits every year than also which having such huge amounts of money and educated minds they can't stop this .Windows created windows updates system which deduct pirated windows and don't let them download updates but now they are few tricks which makes pirated window genuine and you can download updates easily .
Do you think that can anyone stop piracy ,I don't think so ,Almost Everyone is pirated even me . So how many of you are pirated just tell me in comments . And what do you think about pirate world .
Monday, March 05, 2007
Rename Recycle Bin
1. First click on start button and click on run command .
2. Than type ( Regedit ) and hit enter after that you will registry editor window on your screen .
3. After that on left side you will see folders just double click on HKEY_CURRENT_USER folder 4. Now in new folder double click on software folder .
5. Now you will find Microsoft folder double click on that .
6. Now double click on windows folder .
7. Now click on Current version folder .
8. Now click on Explorer folder .
9. Now click on CLSID folder .
Now you will find bunch of few folders , just click on folder named as ( 645FF040-5081-101B-9F08-00AA002F954E)
At last after clicking on this folder you will find folder in right hand side window , just double click on the Default Option and write the name what you want for your recycle bin . I have renamed my recycle bin as kude ka dabba (scrap box) .
After that click ok and go to desktop and refresh it and you will find your recycle bin renamed .
Friday, March 02, 2007
Iconix Fake email Indicator
It works in 3 steps :-
1. Authentication - When an email arrives Iconix use standard technology to verify the authenticity of th message .They use technology like domain keys and Sender ID .
2. Identification -Than email sender is crossed checked by Iconix sender list .
3. Display :- Once an email has passed Authentication and Identification steps, a Truemark icon is displayed in your inbox. Download Iconix free












